Encryption is everywhere online; it’s the process and technologies that enable you to securely log into your email and make online purchases
What types of information are you sending in emails or via website connections? What are you storing on your company servers? Inquiring minds want to know — namely, cybercriminals.
Data from Orca Security shows that more than one-third (36%) of organizations don’t bother encrypting the sensitive data they store in the cloud. This includes data such as intellectual property to customers or employees’ personally identifiable information (PII).
We’ve seen multiple instances of security issues this year involving unencrypted data:
One way to fight back against cybercriminals is to use encryption to secure your data. But what is encryption? I mean, what does encryption mean, both in the sense of what it does and how it secures your data and communications?
Let’s hash it out.
What Does Encryption Mean? A Quick Data Encryption Definition & Meaning
Encryption is the process of taking plaintext data and transforming it into something random and unreadable. Why? It’s a way to secretly share information by restricting access to it. This way, only your intended recipient (i.e., whoever you want to read the message) can access it and no one else can.
Encryption involves using two specific types of cryptographic tools:
- Encryption algorithms (which need to meet specific cryptographic security standards)
- Encryption key (which needs to be securely generated)
Looks simple enough, right? Appearances can be deceiving. The way cryptographic processes work in the background is a lot more complicated than how it appears on the surface. When you encrypt a message on the internet, you’re using a special string of randomized data called a cryptographic key. Keys can either be a set of two unique keys (asymmetric keys), or a single key (symmetric key) that encrypts and decrypts data. We’ll speak more on asymmetric and symmetric key encryption a little later.
When applied, the key disguises your message by turning it into gibberish. This ensures that only the person who holds a corresponding secret key (i.e., your intended recipient) can read the message through a process known as decryption.
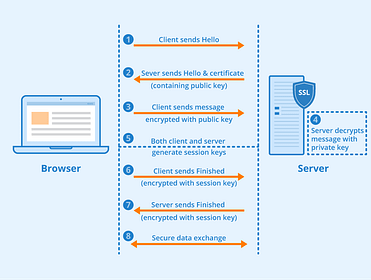
The following illustration shows a basic overview of what the process looks like when sending a secure, encrypted message:

So, how do you know if a website is using a secure connection? It’s got a little padlock icon or another security indicator displaying in the browser’s URL bar:

We’ll delve more into that in just another minute or two. But first, there’s one important thing we want to touch on before moving on to talking about what encryption does…
Secure ≠ Safe
When people see the padlock icon in their browser, they typically assume it means the website they’re using is safe. That’s not necessarily true. You can still have a website that uses a secure connection but it’s not safe because the site is controlled by one or more cybercriminals. This is why we always tell people that a secure website isn’t necessarily a safe website.
The way to help customers ensure that they’re connecting to your legitimate website is to add digital identity to the equation. Your digital identity is like your passport; it’s a verifiable way for people who don’t know you to feel confident doing business with you. This is because you have a trusted third party (a certificate authority) vouching that you’re authentic — that you really are (insert your company’s name here).
You can add digital identity by installing a website security certificate, or what’s otherwise known as an SSL/TLS certificate, on your server. This will enable data to transmit using the secure HTTPS (hypertext transport protocol secure) protocol instead of the insecure HTTP.
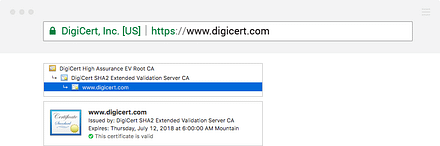
Here’s a quick example of what an extended validation (EV) SSL/TLS certificate looks like in Google Chrome:

SSL/TLS certificates come in three validation levels: domain validation (DV), organization validation (OV), and extended validation. They rank from lowest to highest in terms of the digital identity assurance they offer (hence why EV certificates are sometimes called high assurance certificates).
Why You Need to Secure Your Data
There are several reasons why your organization needs to secure your data and communication channels:
- You’re required to do so for compliance. Depending on your industry or geographic region, it’s likely that there’s at least one data security regulation or law in place that requires you to secure your data using encryption.
- You want to protect your reputation. The importance of your brand and reputation can’t be overstated. Not encrypting your data is a surefire way to get yourself some unwanted publicity. If you don’t secure your data, it’s likely just a matter of time before it falls into cybercriminals’ hands.
- Customer trust matters to you. Encrypting your data goes a long way in helping you develop relationships with customers. If they know that you do all you can to keep their data safe, they’ll be more likely to want to do business with you. If you don’t and let it be known that you’ve had a cybersecurity incident, nearly one-third say they won’t do business with you.
- Fines, penalties, and lawsuits don’t appeal to you. Don’t spend money on fines, penalties, and lawyers if you don’t have to. You can avoid many situations where you’d face these things by securing your sensitive data.
- It’s the right thing to do. There’s something to be said for just doing the right thing because it’s the right thing to do. Protecting the data that people and other organizations have entrusted you to protect definitely fits into that category.
Encryption Secures Your Sensitive Transmitting and/or Resting Data
Encryption can be used to encrypt everything from data sitting in your databases to the data that streams from the IoT devices on your network. Without encryption, every day would be open season on your most sensitive data. This is why organizations should use encryption to protect sensitive data at all times.
Protecting Data in Transit from Man-in-the-Middle Attackers
Data in transit encryption can be used to secure your data while it’s moving between endpoints. A great example of in-transit data encryption can be seen when your customers’ browsers send information to your web server. This is known as in-transit data encryption, which protects you from interception attacks (i.e., man-in-the-middle attacks).
Good examples of this are secure SSL/TLS website connections. If you don’t secure your website using an SSL/TLS certificate, cybercriminals could simply wait for your customers to log in to your website and steal their credentials. They do this by intercepting the data, placing themselves in the middle of your connection so all data flows between the customer and the server through them.
Not only does this spell bad news for your customers, but it’ll be bad news for you since they’ll no longer trust you to protect their data.
Keeping Your At-Rest Data Safe On Your Servers
If your data is sitting on your server, that automatically means it’s safe from attackers, right? Not necessarily. Data at rest encryption plays an important role in keeping the data sitting in your databases, inboxes, and other important repositories secure. For example, if someone hacks your email server, any unencrypted messages are at risk of compromise.
Encrypted Data Is Meant to Be Decrypted…
Yes, you read that correctly: Encryption is known as a two-way function because encrypted data is meant to be decrypted by someone who has the appropriate key. When you encrypt something, you need to use a key to decrypt that data. In asymmetric encryption, you have two separate keys and each key performs a separate function (one encrypts, one decrypts). In symmetric encryption, it’s a single key that performs both functions.
It’s important to note that encryption algorithms differ from hash ciphers. While encryption ciphers are meant to be reversed, hash algorithms are designed to serve as one-way functions. Their resulting strings of data are not intended to be reverse-engineered [and, frankly, it’s too impractical to try to do so]). And instead of being used to encrypt data, they’re used as data integrity mechanisms to prove that data hasn’t been altered since it was digitally signed.
Encryption is a way for two parties to communicate securely. Historically, this meant two parties would have to meet face to face to securely exchange keys. They’d use the same key to encrypt and decrypt information. This is an example of a type of encryption known as symmetric encryption. Also known as private key cryptography, this approach entails using a single key to scramble and unscramble your messages.
Here’s a basic look at how encryption and decryption work using symmetric (matching) keys:

Of course, the encryption ciphers we use to communicate over the internet are far more complex than the simple example we’ve provided above. However, the graphic gives you the basic idea of the concepts of encryption and decryption.
Symmetric Encryption Has Been the Go-To Method Throughout History
Symmetric encryption is nothing new; it’s been around for thousands of years, dating back to at least ancient Egypt. It’s the old, trusted war horse of cryptography and it’s had many reinventions over its lifetime.
When I was a kid, I had out-of-state cousins who would come to visit my family. My cousins and I would exchange handwritten letters, and one of my cousins used to write brief messages in ciphertext. It was a basic shift cipher (AKA a Caesar cipher), meaning that you just shift a letter by one or more characters in the alphabet. The number of movements is determined by a secret key that only we would know. (This way, her siblings and mine couldn’t read our messages.)
For example, if we used a key of 6, then “a” would become “g” and so on. So, if the cousin wrote the word “beach” and used a key of 6, then it would become “hkgin.” Because we both had knowledge of the key, this is a basic example of how it looks when you use symmetric encryption.
Traditional (Symmetric) Encryption Can’t Stand on Its Own in an Internet World
We live in a time when the internet has become integral to businesses. This invention is a double-edged sword; it’s great because companies can engage in remote, near-instantaneous communications. But that also means that no one wants to hop on a plane and fly halfway around the world every time they need to do a transaction.
But why would you need to do this? Because the internet is inherently insecure. It’s an open public network that sends plaintext data, meaning that your sensitive information can be intercepted by bad guys who can use it to carry out all kinds of evil (data theft, identity theft, fraudulent transactions — the list goes on). This is why industry experts had to come up with a way for people to communicate securely without having to first meet up to exchange symmetric encryption keys.
Why Asymmetric Encryption Is Essential to Secure Online Communications
In a nutshell, asymmetric encryption (i.e., public key encryption) enables people to communicate remotely without having to meet up in person. This type of encryption uses a pair of unique (but mathematically related) keys to carry out the encryption and decryption processes.
People call it by different names, but this type of encryption boils down to the following breakdown:
- The sending party encrypts the message using their public key.
- The receiving party decrypts the message using the corresponding (separate) secret key.
What this does is enable you to communicate data in open channels (public and insecure networks), such as on the Internet. Here’s a look at how this process works from a little more technical perspective:

Think of the last time you made an online purchase. When establishing the website connection, your browser reached out to the website’s server. The two parties exchanged some key information (literally and figuratively speaking) that they used to exchange a session key. This key is what they then used the rest of the session to communicate because it required fewer resources than an asymmetric connection.
Asymmetric vs Symmetric Encryption: Is One Better Than the Other?
It’s not so much a question of which one is better; asymmetric and symmetric encryption both play important roles in securing online data and communications. Quite frankly, you need both to achieve secure website connections:
- You use asymmetric encryption to securely exchange key-related information
- You use that shared key information to create a secure symmetric session that can be used to communicate the rest of the session
You use asymmetric first because it’s a secure way to share your symmetric keys on the (insecure) internet. But asymmetric algorithms require a lot of resources, meaning they’re not great at scale (i.e., enterprises handling massive traffic). So, the smarter idea would be to use asymmetric algorithms at the beginning and then switch to symmetric algorithms that are less taxing at scale.
The More Important Considerations Are Key Security and Certificate Management
The encryption algorithms you use are only as good as the security you use to protect your cryptographic keys. If even one of your cryptographic keys gets exposed, then you’re in for a world of hurt because it means that every bit of data that key encrypted is now at risk of compromise. For example, this could be the case if you didn’t use algorithms that enabled perfect forward secrecy.
Furthermore, you also need to carefully track and manage all of the certificates in your environment. If even one certificate expires and is still used on your website, for example, then it means:
- Users see ugly “not secure” warning messages on your website
- All data that transmits to your website is insecure
Final Thoughts on What Encryption Means
As you can see, answering the question “what is encryption?” in the simplest terms isn’t always easy, but we gave it our best shot. (It’s easy to overthink things.) Hopefully, you’ve found this article both informative and useful as you go about your day. The big takeaways we want you to leave with include the following:
- Encryption is a common cryptographic process for disguising or concealing data
- Encryption secures your data both in transit (think SSL/TLS) and at rest (think of emails on your server)
- It can be done using unique keys (symmetric encryption) or identical key pairs (symmetric encryption)
- For encryption to work, you must carefully manage your certificates and keys
Article published on TheSSLStore by Casey Crane